JEB Decompiler for RISC-V
Cut down on reverse engineering time: use our interactive RISC-V decompilers to analyze RV32/RV64 binaries.
RISC-V plugins features:
- Code object files: support RISC-V in Linux ELF, Windows PE, or headless code (e.g. firmware).
- Disassembler: support for RV32/RV64, regular and compressed opcodes for the following ISA extensions: I (integer), Zifencei, Zicsr, M (multiply), A (atomic), F (single-float), D (double-float), C (compressed). Note that RV128, RVE (embedded) and other more "exotic" extensions (mem tx, simd, vectors, etc.) are currently not supported.
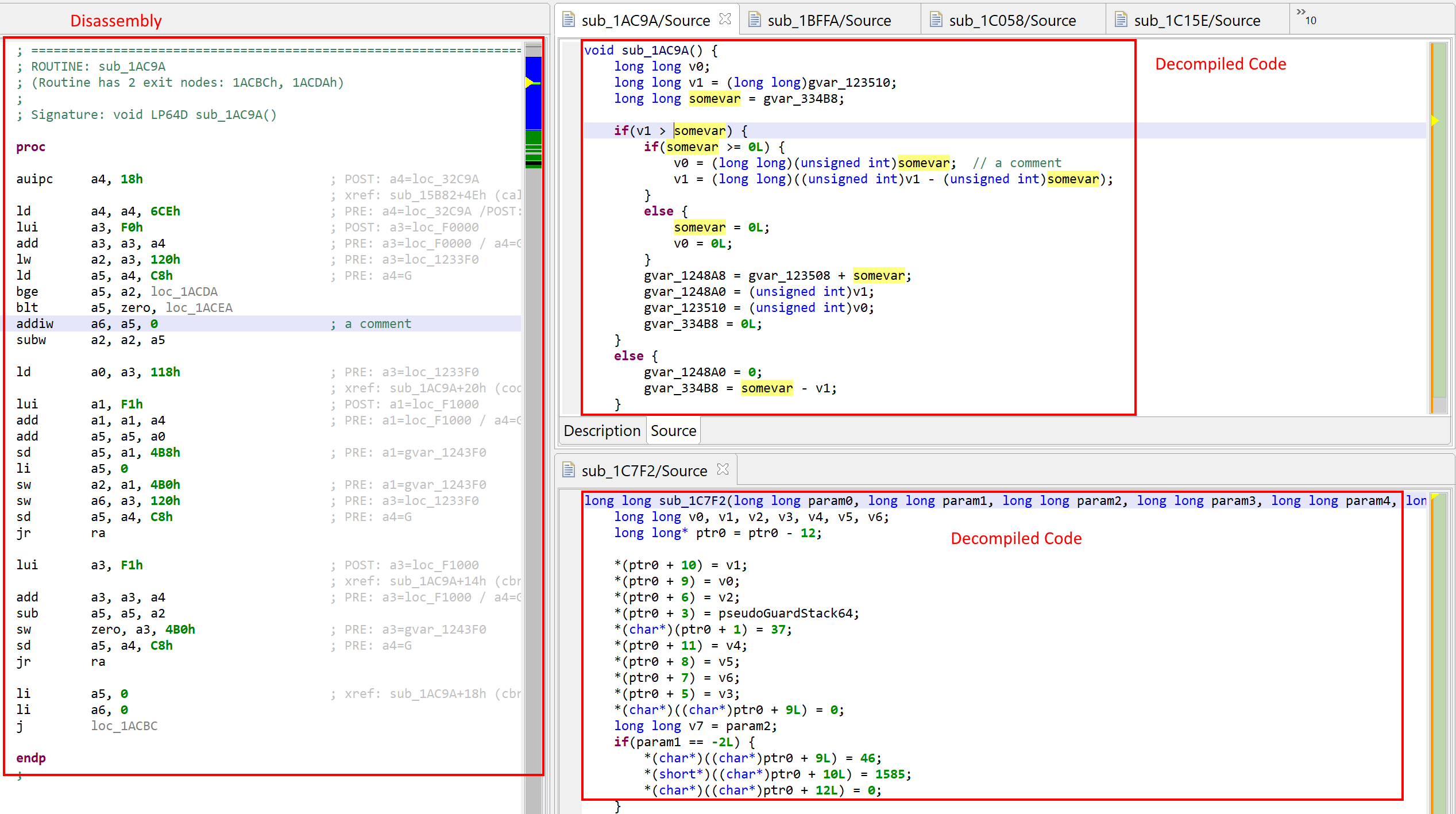
- Decompilation: support for RVI (decompilation of the integer/general-purpose operations) for 32-bit and 64-bit. Decompiler support for F/D extensions (floating-point instructions) is a planned addition.
- Relocations: support for common ELF relocations specific to RISC-V. Common PLT resolver stubs are handled.
- Calling conventions: calling conventions ILP32D and LP64D are supported. Custom calling conventions can be defined.
- Type libraries: ARM or MIPS type libraries for Linux 32/64 or Windows 32/64 can be reused.
A non-exhaustive list of other JEB features shared by all native code plugins (not specific to RISC-V):
- Interactive layer offered by the GUI client, allowing refactoring: renaming/commenting/cross-referencing, type definition, stackframe building, etc.
- Advanced analysis to detect tail-calls, non-returning methods, switch-like idioms, etc.
- Advanced decompiler optimization passes to thwart protected or obfuscated code. Power users can craft their own IR optimizers (example)
- Type libraries for efficient file analysis. JEB ships with typelibs for win32, winddk, linux glibc, android-linux, etc. Power-users can generate their own typelibs as well (details)
- Traditional signature libraries of common SDK, including all versions of Microsoft Visual Studio runtimes, the Android NDK, etc.
- Codeless signature libraries for common libraries used in malicious and clean applications alike, such as openssl, libssh2, libcurl, etc.
- Full API and access to the Intermediate Representations to perform advanced and/or automated code analysis in Python or Java (details)
- Safe emulation for in-place decryption of obfuscated code.
Example: Debian RISC-V 64-bit, unzip program (click to expand to a full JEB window view)