The Bluebox fellows have posted an interesting Android crackme a few days ago.
The APK presents several oddities, including:
- APK entries marked as password-protected.
- Reuse of java.lang.String to confuse tools and analysts.
- Some basic cryptography in the APK.
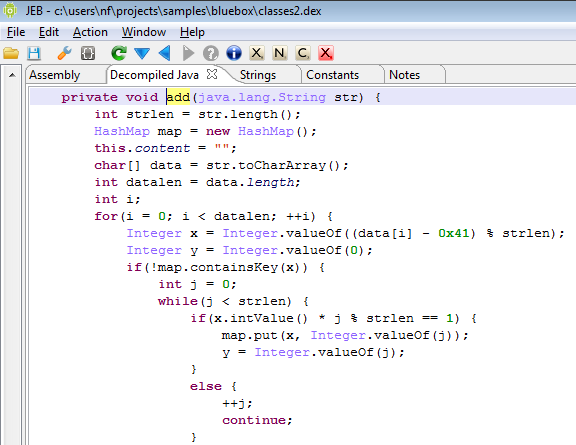
- The most interesting part: a native library that replaces the bytecode for the custom String.add() upon loading the main activity class
As Jurriaan Bremer pointed out, the replacement bytecode in question can be found at offset 4004h of libnet.so, and is E0h bytes long. The original String.add() is only A6h bytes long, and references exception handlers. Replacing the bytecode is not trivial, but annoying.
After reassembly, JEB decompiles the real String.add() to clean code: (marked-up in the screenshot below)
I’m providing the sources for both com.bluebox.lab.poc.Action and the fixed java.lang.String if you want to complete the challenge.
Enjoy.