We have released and open-sourced Androsig, a JEB plugin that can be used to sign and match library code for Android applications. That plugin was written by our summer intern, Ruoxiao Wang.
The purpose of the plugin is to help deobfuscate lightly-obfuscated applications that perform name mangling and hierarchy flattening (such as Proguard and other common Java and Dalvik protectors). Using our generic collection of signatures for common libraries, library code can be recognized; methods and classes can be renamed; package hierarchies can be rebuilt.
Example on a random obfuscated application, obfuscated by Proguard, before and after matching:

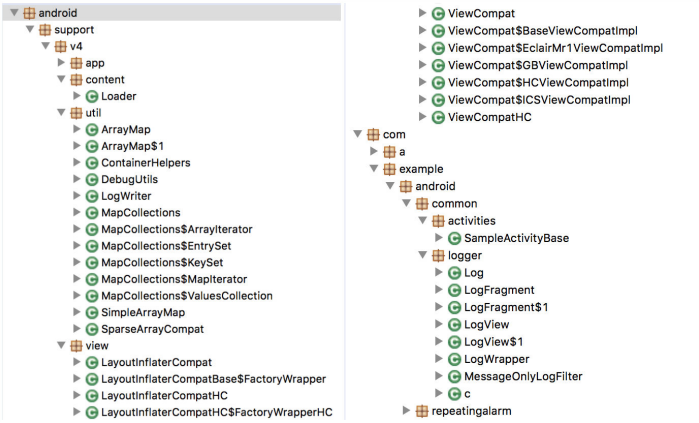
Installation
First, download the latest version of the compiled binary JebAndroidSigPlugin-x.y.z.jar and drop it into the JEB coreplugins/ folder. You will need a JEB Pro license for the plugin to operate.
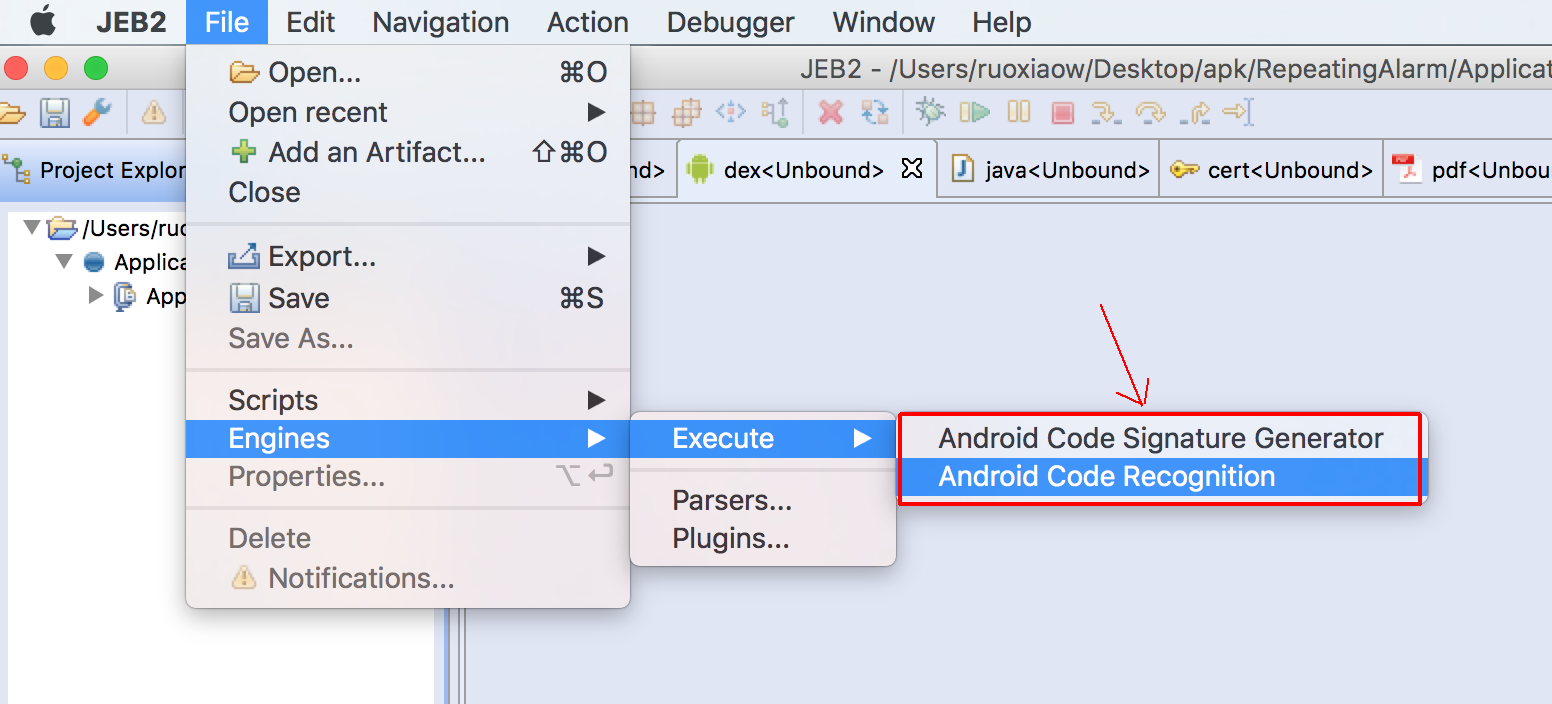
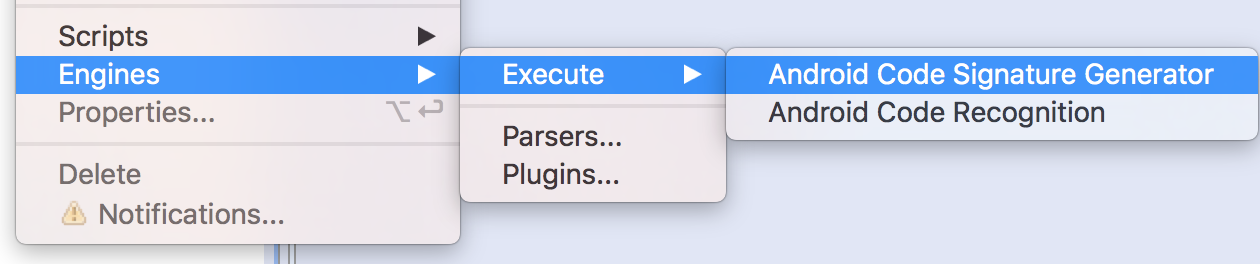
This single JAR offers two plugin entry-points, as can be seen in the picture below:
Secondly, download a bundle of signatures for various versions of the most common Android library.
Link to signatures library archive.
Reference: list of library signatures contained in this archive
Extract the contents of the archive into the coreplugins/android_sigs/ folder.
Matching obfuscated code
- Open an Android APK or Dalvik DEX file to be analyzed
- Execute the Android Code Recognition engines plugin
- Customize the matching parameters, if necessary (See below for details)
- Press OK. The code will be analyzed, and methods and classes that match signatures present in the database will be renamed and refactored.
Generating signatures
Generating your own library signatures (for library code, analyzed malware, or else) is as easy as its matching counterpart.
- Open the APK containing the code to be signed
- Execute the “Android Code Recognition” engines plugin
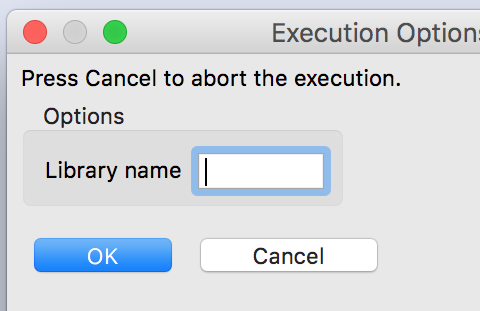
- Specify the library name and other options
- Press OK. The signature *.sig file will be created in the coreplugins/android_sigs/ folder. (Always make sure that all your signature files are in that folder.)
About the Matching Results
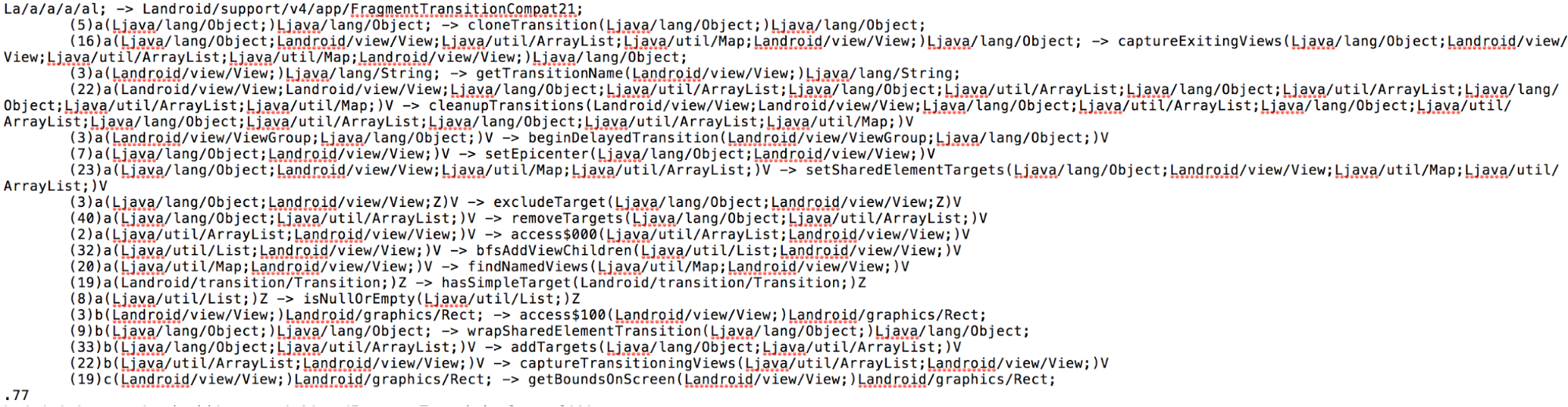
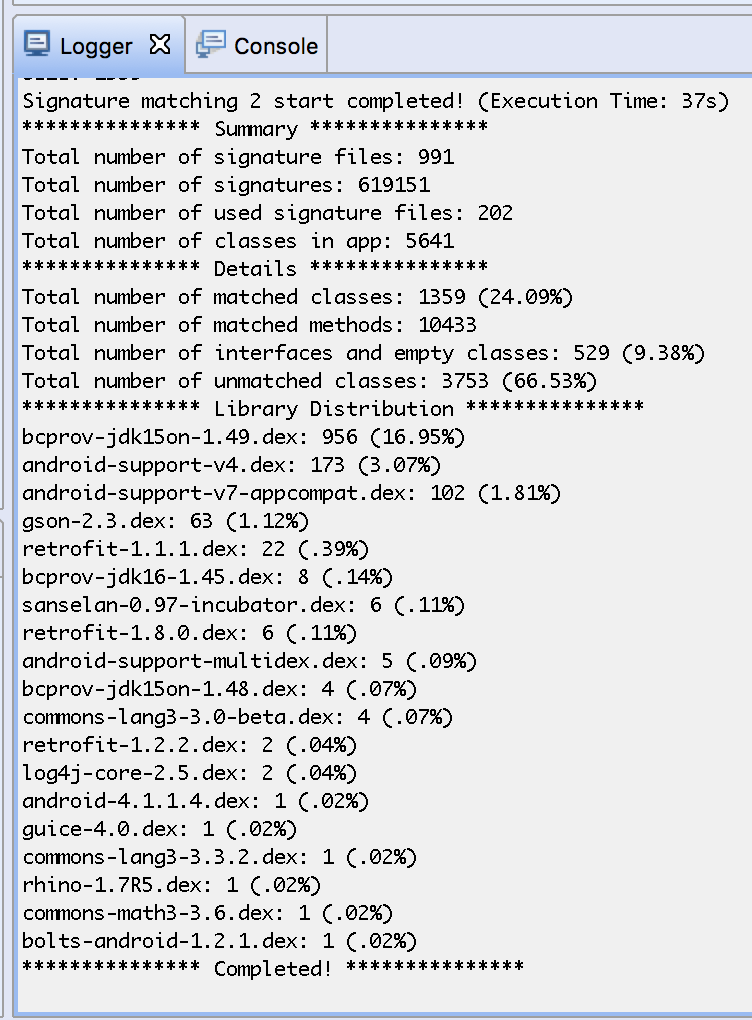
Upon successful execution, the matching plugin will generate two files in the temporary folder: androsig-mapping.txt and androsig-report.txt.
The mapping file shows which obfuscated methods and classes were matched, and to what:
The report file gives you a summary of how many methods and classes were unmatched and matched, where they are coming from, as well as library distribution code. That result data is also output to the JEB logger:
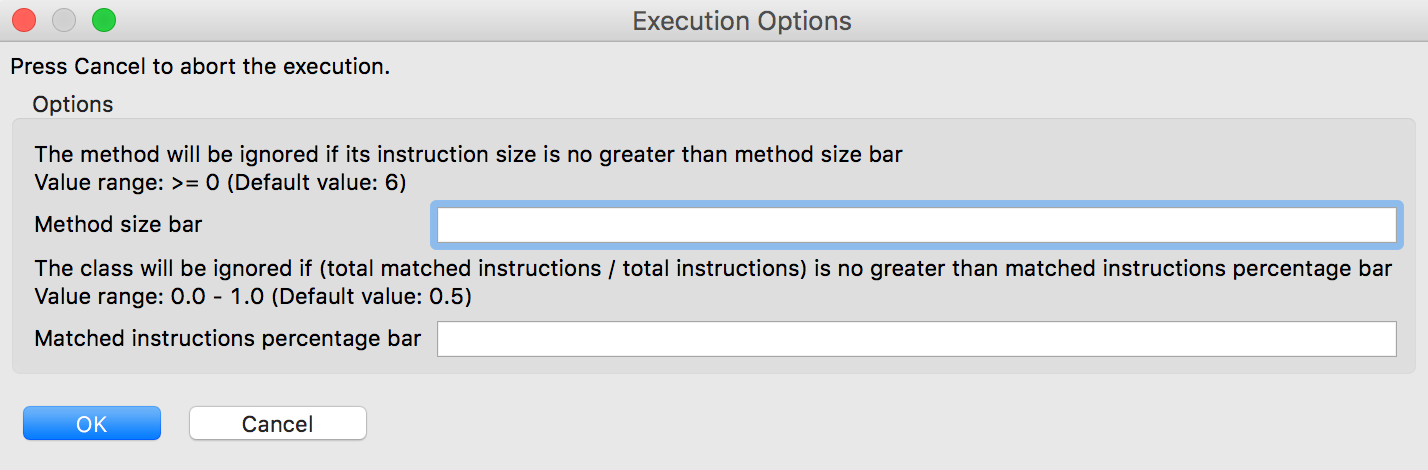
About the Matching Parameters
The matching process can be customized by two parameters, as shown on the picture below:
For most use cases, the default values will suffice. However, both parameters can be fine tuned to have more aggressive or less aggressive (looser) matching:
- More aggressive matching will result in more matches, at the expense of false positives (FP in this context refer to methods or classes incorrectly matched)
- Looser matching will result in less matches, at the expense of false negatives (FN in this context refer to methods or classes that should have been matched)
Typically, false positives happen on either small methods or classes containing lots of unmatched methods. Experiment with those parameters if need be; as said, the defaults generally yield correct results.
Also feel free to customize the plugin if need be, or use it as a learning tool and tutorial in order to bootstrap your own plugins development needs. It is by no means a robust plugin, but should help reverse engineers focus on code that matters (that is, non-library code) in the case of many Android applications.

liuchangqing
I’d would purchase JEB in a heartbeat if you had a personal lic for ~100$. Unfortunetly its ways to expensive so I will stick with jadx.
I have bussiness license. I followed the instructions but when I check File->Engines->Execute menu it is empty.
I also is same, can someone to solve this problem?